I’m currently digging the heatmap that Strava produces with running route data.
more “Data is Beautiful, Episode #1: Strava Running Routes”
SAML – the standard that wasn’t

SAML – the Security Assertion Markup Language is quite successful. SAML was born in 2002 out of OASIS, the somnolent standards body that enjoyed its heyday in the 2000’s forming so many of the XML-oriented standards like WS-BPEL, UDDI, UBL, and ODF. Today SAML enjoys success satisfying a key need in enterprises: browser-based single-sign across origins. Sign into www.mycompany.com and then later visit www.serviceprovider.com and get automatically authorized. The benefit is: people type in their passwords, just once.
SAML wasn’t designed for just that problem, or anyway, not for that specific problem. SAML was designed to address the general problem of exchanging claims securely. The summary on the first page of the spec says that SAML “defines the syntax and semantics for XML-encoded assertions about authentication, attributes, and authorization, and for the protocols that convey this information.” Hence the name, “Security Assertion Markup Language”. But in actual use, SAML is heavily oriented towards browser-based SSO.
In SAML, the claims or assertions are statements about people. When people (via apps or browser pages) make requests of systems – like “let me see this file”, or “let me transfer funds” – the system that receives this request can use trusted claims about the requester to make authorization decisions. The key is that the system needs to trust the claims, and the claims need to be relevant.
An example: If I go to the grocery store, I can present my debit card to the checkout person, to pay for my groceries. The card is basically a set of claims “asserted” by a bank about me:

- that the person named on the card is a customer of the bank,
- that the person named is authorized to use a particular account.
This set of assertions is also decorated with some other information, like valid dates, and the author of the claims. The author of the claims is a bank, and that bank is affiliated with a card payment network, in my case, Visa. Also: My debit card expires in a given month and year. The implicit rule is that all parties agree that the claims presented in the plastic card do not hold after that date. This card is good if the merchant trusts the bank, and Visa, and if the dates are valid. Some merchants want to insure that the person named on the card is the same as the person presenting the card, so they’ll ask for a government-issued picture ID that has the same name.
The SAML Analogue

SAML works in a similar way, except the set of claims is formatted digitally, in an XML document, rather than on a plastic card. The set of claims enclosed in a SAML token is general – it can be any set of claims about a person, or “subject”. Claims such as “Dino is male”, or “Dino has no tattoos”, or “Dino is of sound mind and body” are all acceptable. But more often the claims are statements that are relevant to information-processing organizations, such as “Dino is an employee of XYZ corp.” and then some detailed information such as “Dino’s email address is Dino@xyzcorp.com”, “Dino is a member of the Aviation group in XYZ”, and so on. In the general case these are claims about a person’s identity; SAML calls them “Attributes” of the subject. Statements not about the particular person don’t belong in SAML. “It is sunny today” may or may not be true but it is completely unrelated to me – the person in question aka “subject” – therefore not suitable as an attribute in a SAML assertion about me.
Such claims about me could be used by an organization or company to decide whether to grant service to me, when I request it. If my company, XYZ corp, has a partnership agreement with another company, LMN Corp, then when I present my claims to LMN, along with my request, LMN can take a decision on whether to grant my request.
How Trustworthy are your claims?
The claims in a SAML Assertion are just statements, coded in an XML document. Though SAML is a particularly florid and ornate language, it’s still XML, and anyone could create such a document. For a system to be able to rely on that information, to trust that information, there must be some assurance that the presented claims are bona-fide and originate from a trusted source, and also that they are valid at a given moment in time. At one point, “Dino is in the Eighth grade” was a true statement about me, but that statement is no longer true. SAML uses digital signatures based on public-key cryptography for the purpose of assurances of the author of the claims, and explicit time windows on claims (eg, NotBefore or NotOnOrAfter) to circumscribe the validity of such claims.

The “Relying Party” or RP examining a SAML Assertion SAML must verify the signature on the XML document, to insure that the claims can be trusted. The relying party must also evaluate the time windows on the claims. And then finally, the RP must evaluate the claims themselves. It may be that “Dino is a member of the recreation committee” does not grant me permission to see the early draft of the company’s 10-K filing. On the other hand if I am a senior director at the auditing firm, maybe “Dino is an employee at XYZ Auditors” and “Dino is a senior director” is a good enough claim to allow me to see or edit the document.
Simple in Concept, Complex in Execution
SAML is simple enough in principle. I’ve explained the broad strokes here, in just a few paragraphs. Of course, it builds on a large stack of technologies, starting with XML, XML Schema, XML namespaces, URIs, XML digital signatures, and X.509. That alone is a daunting set of technologies, though there is some relief in the maturity of the relevant specifications.
But the details about SAML itself have lead to additional complexity. First, the SAML 2.0 spec is 86 pages. Even there, it is not self-contained. One example: SAML has an element called an AuthnContextClassRef I’m guessing this implies “Authentication Context Class Reference”. For those of you scoring at home, that’s four nouns in a row. What exactly is this thing?
Helpfully, the OASIS spec defines this thing as
A URI reference identifying an authentication context class that describes the authentication context declaration that follows.
All clear? We now interrupt this essay to present a completely unrelated Dilbert comic.
In addition, the SAML spec document suggests, “See the Authentication Context specification [SAMLAuthnCxt] for a full description of authentication context information.” That document is itself an additional 70 pages. Ready to dive in?
This kind of complexity and standards-speak lead, even early on in the life of SAML, to complaints of impracticality from the people who had hoped to be able to use it. Even as early as 2003, just a few months after SAML 1.0 was launched, IBM, one of the original authors of the spec, was employing its partners to bravely assert that the idea that SAML was complex was a myth.

I can hear the wizard inveighing: Pay no attention to that AuthnContextClassRef!!
But the complaints about complexity were not academic. They were based on real-world attempts to get disparate implementations of “the standard” to interoperate. Even today, connecting an Identity Provider and a Relying Party via SAML is a challenge worthy of a platoon of IBM consultants. Have we got a mismatch in the AuthnContextClassRef? Well, we’re gonna have to figure out how to persuade the Relying Party to allow it, or to persuade the IdP to provide a different one. Have you got the wrong NameID Format? Transient, Permanent or Unspecified? Which side needs to give ground in this negotiation?
That’s what I mean when I call SAML “the standard that wasn’t.” It’s a standard, all right, but there are so many different options that despite the rigor of the specification, getting compliant systems to interoperate is still a huge challenge. Despite the challenges, the standard IS valuable – it works mostly, and it solves specific problems that many companies have. But it isn’t automatic.
Lessons for History
SAML is designed to address much more than browser-based single-sign on. But the lion’s share of adopters use SAML for just that, and only that.
There’s a lesson here regarding over-reach of standards: SAML could have been simpler, quicker to get adopted, and easier to use, had its designers restricted their design goals to addressing what 90% of people use it for today, anyway.
Why Bother?
But why am I even talking about SAML? My passion and intention is to work on APIs and enabling new interconnections. That’s why I’m at Apigee today. APIs means “SOAP on Steroids” or if you like, “all the benefits of SOAP without that unsightly residue”. It means getting better connections, faster, and allowing new customer experiences, better mobile apps, better connections between customers and companies. So if I am all about connecting systems with APIs, why do I care about SAML? Have I been sucked into a time-portal and time-warped back into 2007?
Ah, but no! See, the thing is with large companies, they move deliberately. Many still use SAML and still need any systems they install to integrate with their SAML-based Enterprise Identity system. So if I want to work with enterprises in helping them adopt APIs to supercharge their businesses, I need to get SAML working with the various web apps that enable API management and adoption. Get SAML integration done, then the enterprise can innovate with APIs. See?
FiveThirtyEight just pre-negotiated Lionel Messi’s next contract
FiveThirtyEight shows the data that explains why Lionel Messi is worth more than any other player.
Love me that breakdown.
40% of your Team’s Effort….. Wasted?
Bakadesuyo.com always has interesting material, presented in an attractive, accessible manner. Highly recommended.
I’m currently looooovvvvving this post entitled “40% Of Your Team’s Effort Is Wasted.”
One point that particularly struck me:
Being great is full of unexpected hurdles. So, what you have to have on a team is people who are willing to say “We’re screwing up.” “You’re doing that wrong.” “We need to change.” “We have to do something different — and here’s my idea.”
Anyone out there ever catch a ton of flack for being that guy?
I love having that guy on the team. (or that girl). I love people on the team who, at one point or another, refuse to roll over, refuse to just accept everything as it currently is, and challenge the current plan, even if everyone else would like the current plan to just remain stable for a little bit so they can breathe easy. We’re not at work to breathe easy. We’re at work to solve hard problems, over-constrained problems via creative approaches that deliver imperfect, but close-enough results. We’re here to challenge ourselves! And that’s the fun part, dammnit!
Youknowatumsayin?
Moving to nearlyfreespeech.net – bare domain and www

I moved to nearlyfreespeech.net this week, from 000webhost.com. It is much faster, and now I won’t get popup ads.
While moving the site, I took the opportunity to upgrade to the current WordPress. I think I was on WP3.3 previously; now it’s on the current release. And now I’m on the current PHP, too. Nice.
Everything went pretty well. I had some fun with the wordpress part – updating the existing plugins, using wp-cli, fiddling around with my own plugins which had a few problems using deprecated WordPress functions…, doing surgery on other plugins, now abandoned.
I had to update from the old Twitter widget I had been using; it was still using the Twitter v1 API, which did not use OAuth. This API is no longer supported, so the widget wasn’t able to retrieve any tweets. I found a new one called… really-simple-twitter-feed-widget. And it was pretty simple, in the end. But I did have a problem: when pasting my token secret into the configuration box, I inadvertently had grabbed a leading space. Instead of pasting “XYZABC” as the token, I had pasted “_XYZABC”. But I didn’t realize this, because the textbox was masked, and all I saw was those dots.
The incorrect token secret caused all of the signatures generated by the widget to be invalid; therefore the Twitter API was rejecting them. I had to crack into *that* code as well, to diagnose this. Only printing out the token secret just before it was used to generate the OAuth1.0a signature showed me the light. After that, the new Twitter widget just worked! Sweet!
Finally, I got all the PHP squared away.
NFS is a cheap hoster, but easy? No. I don’t mind the lack of cPanel. I love the SSH access to my machine. Everything is possible on NFS; the trick is figuring out HOW to do stuff.
The last thing I got stuck on, in the move to NFS, was configuring http://dinochiesa.net to redirect to www.dinochiesa.net. The FAQ for NFS says that you can do it using “a hard canonical name”. But doesn’t say HOW to make that effective. Back and forth through the FAQ on the NFS site, to no avail.
At last, this blog post helped me.
- Go to the Nearlyfreespeech UI ->Site->Select the site in question->Add a new alias e.g. dinochiesa.net
- Once dinochiesa.net appears under the Site Name and Aliases table in the site menu, click the “Set Canonical Name” (on the menu on the right)
- Select HARD Canonical settings and select www.dinochiesa.net
Thanks, Keith! I don’t know why this isn’t in the FAQ doc for NFS.
Comparing Graphite and Flot
Producing a dashboard with charts generated by Graphite using its render API I kinda liked the results:

But then I thought, I wonder if I could produce the same dashboard from the raw data, using jquery flot?. And the answer is, of course:

Which do you prefer? I kinda like the flot version better. As a developer, I have finer control over the look of the chart. This means, for one thing, the fonts are nicer. Also, I can move the title around, style things differently. And I can make the chart interactive, too. Using graphite involves significantly less labor, though. Less custom code.
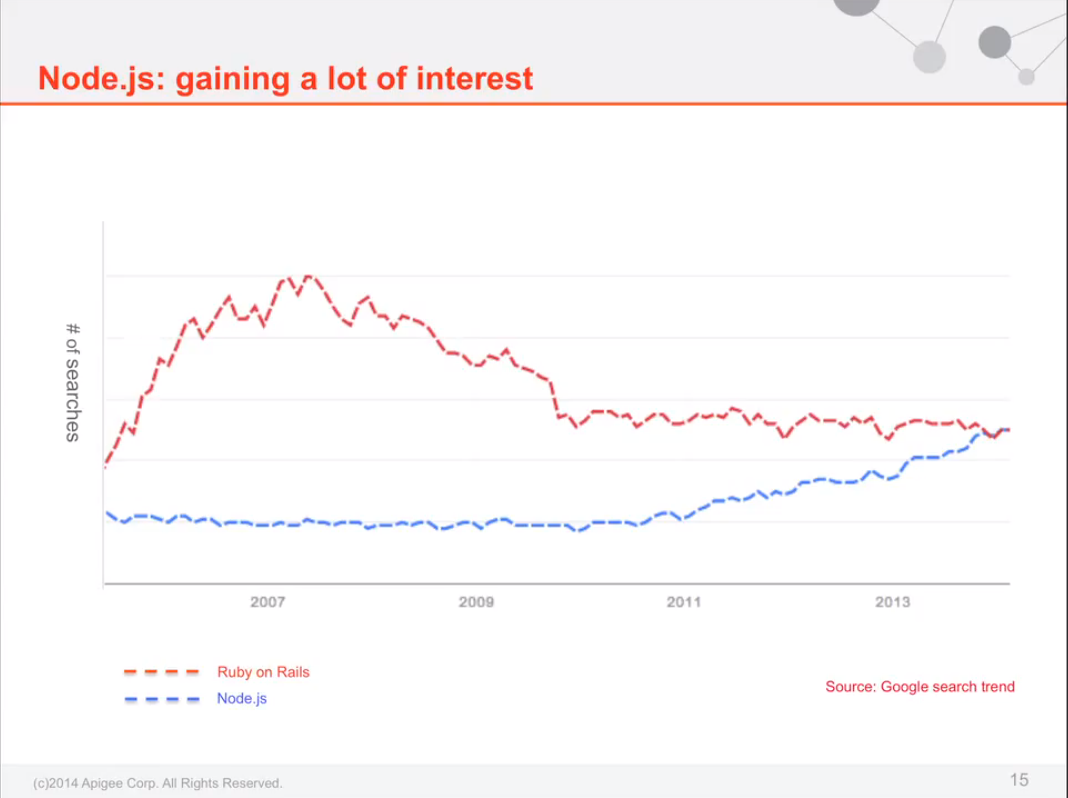
NodeJS vs Ruby on Rails popularity
Everybody’s favorite indicator, the Google search trend chart, shows that Nodejs is overtaking Ruby on Rails:
Welcome to 1998, Apple! JavaScript will soon be usable for automating OSX apps
via Reddit, I learned that Apple is introducing JavaScript as a way to automate inter-app communication in OSX. JavaScript continues it’s growth.
Just a couple notes:
- Windows had this in 1998 with WSH which was first available in Windows 98. Just sayin.
- Microsoft has also recently published a sample for using JavaScript as a scripting language for any .NET app. Kewl.
I don’t really hate NodeJS
I don’t really hate NodeJS. Yes, a while ago, I said I hate NodeJS. But I didn’t really mean it. I was just suffering from unrealistic expectations. I learned to Let Go of my idea that JavaScript on MacOSX ought to be as easy as JS on Windows.
Since then I have adopted NodeJS pretty strongly. I use it for all sorts of tasks, from tools that automate Apigee Edge (nod to my employer) to API load generation utilities.
I write more code using NodeJS these days, than in anything else.
Recently I had occasion to write a little utility that computes TP99 for a set of API transactions being managed by Apigee Edge.

For this tool, I chose NOT to use NodeJS but instead relied on good-old PERL. I didn’t want asynchrony, and I did want easy file I/O, pattern matching, and sorting. Also I wanted it to be maintainable by old-school sysadmins who no-doubt have not been following the finer points of using Q’s promises in NodeJS. Perl was the obvious choice. The sort required to compute TP99 will run on 60000 records or more, and needs to occur every minute, for all transactions logged during that minute. A cron job running a perl script was perfect for this.
But, recently I wrote another tool… this one automates the provisioning of EC2 instances in AWS, then installs Java and Apigee Edge on them, and configures them into a cluster. I wouldn’t want to do that in perl or Bash. NodeJS was the right tool for that much more complicated job. And of course there are NPM libraries for AWS, and for ssh and scp. Really helpful.
of nodejs and new clothes

A provocative post by Eric Jiang, entitles “The emperor’s new clothes were built with Node.js”, regarding the undeserved praise being heaped upon NodeJS. While I think he gets his analysis all right, he is still missing the forest for the trees.
Nodejs has grown the way it has grown for the same reason that Visual Basic and PHP grew the way they did: These things work well, and help people get things done quickly and relatively easily. And maybe, people even have fun doing it. The community support has been critical in all three cases.
Sure it’d be nice to have multi-threading like Go and a single set of known and blessed libraries like C# and performance like C. But we don’t have all those things in one package, not yet anyway.
There are weaknesses in NodeJS, just as there are in PHP and in VB. Despite that, JavaScript is effective for many many people, and will continue to be so. NodeJS makes JavaScript much, much more effective with the NPM and the vast set of downloadable modules.
No religion, yo: nodejs is not always the right choice. Of course it isn’t. I like nodejs and use it… daily. but I’m learning Go and am enjoying that as well.


